Healthcare Compliance Professionals Grapple with Mounting Risks and Limited Resources
HIT Consultant
NOVEMBER 7, 2024
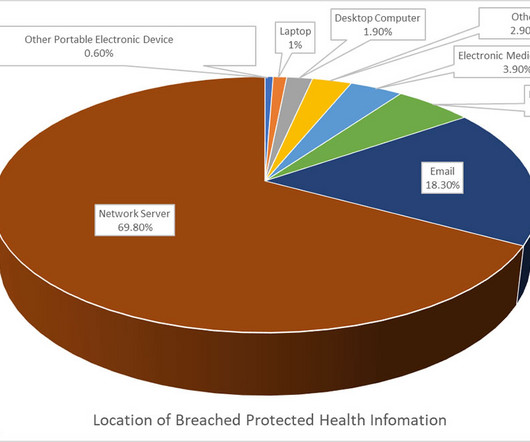
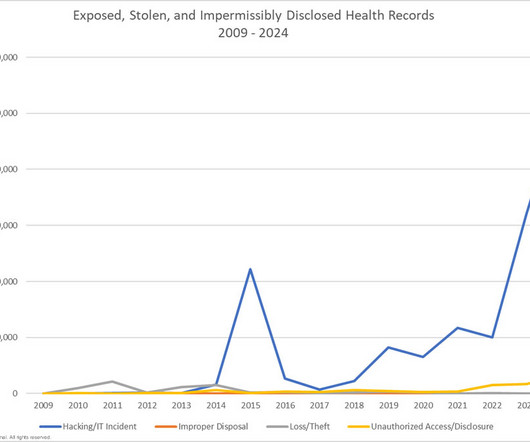
What You Should Know: – A new report from Barnes & Thornburg reveals that healthcare compliance professionals are facing mounting pressure as they navigate a complex regulatory landscape, increasing cyberattacks, and the rapid adoption of artificial intelligence (AI).


















Let's personalize your content